这道题会给我们一个exe文件,打开是一个判断输入的密码是否正确的软件:
我们用IDA打开它,会发现并没有反编译出main()函数。所以我们随便输入一点内容试一下: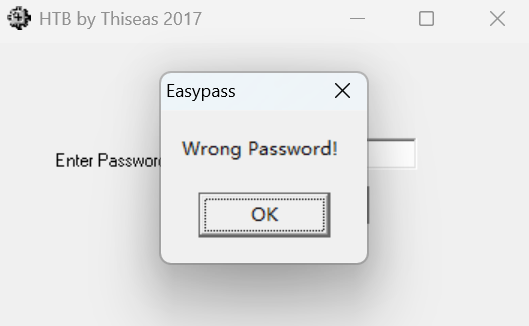
会返回Wrong Password!字样。接着我们尝试用IDA搜索这段内容,会发现: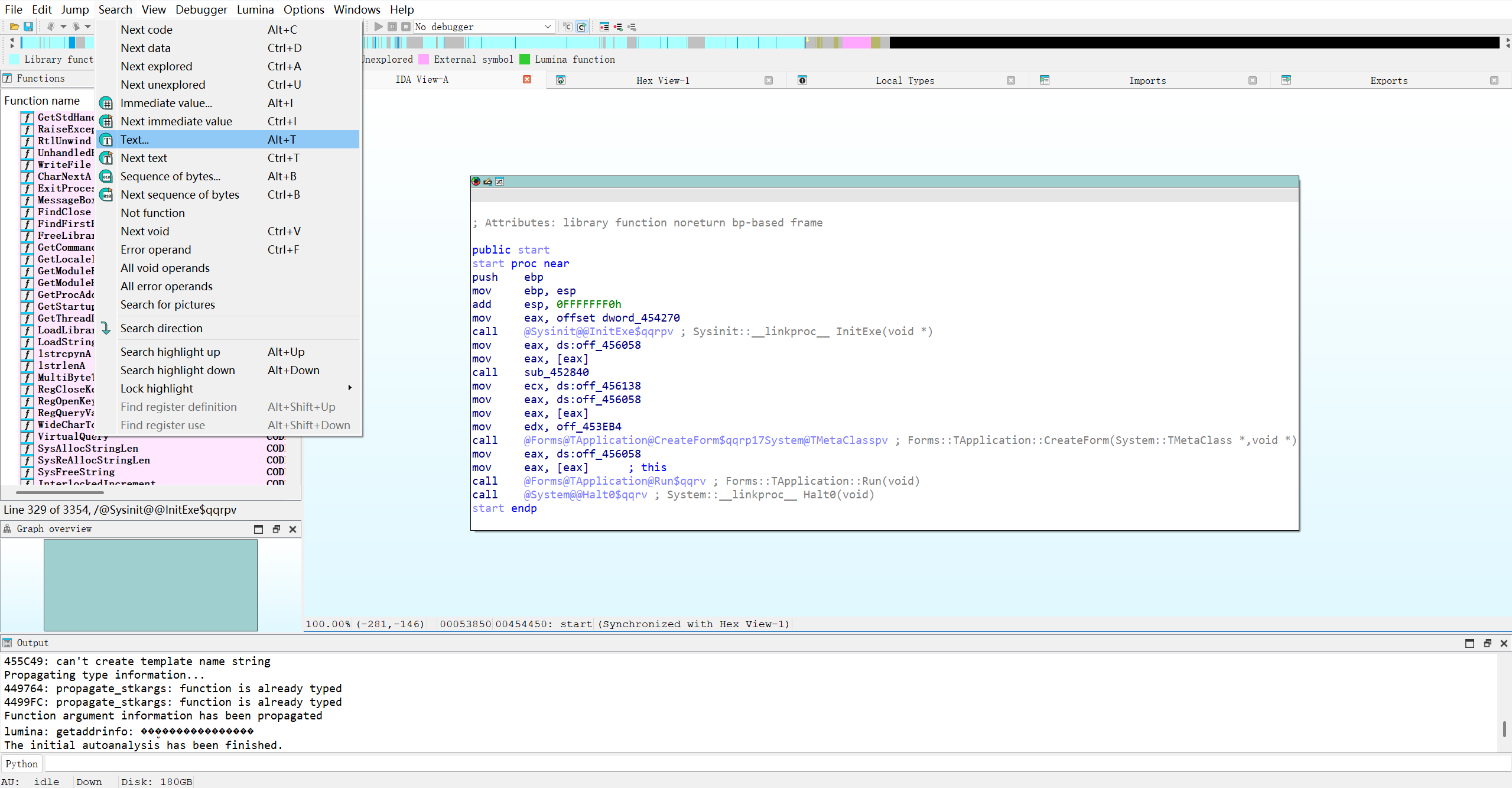
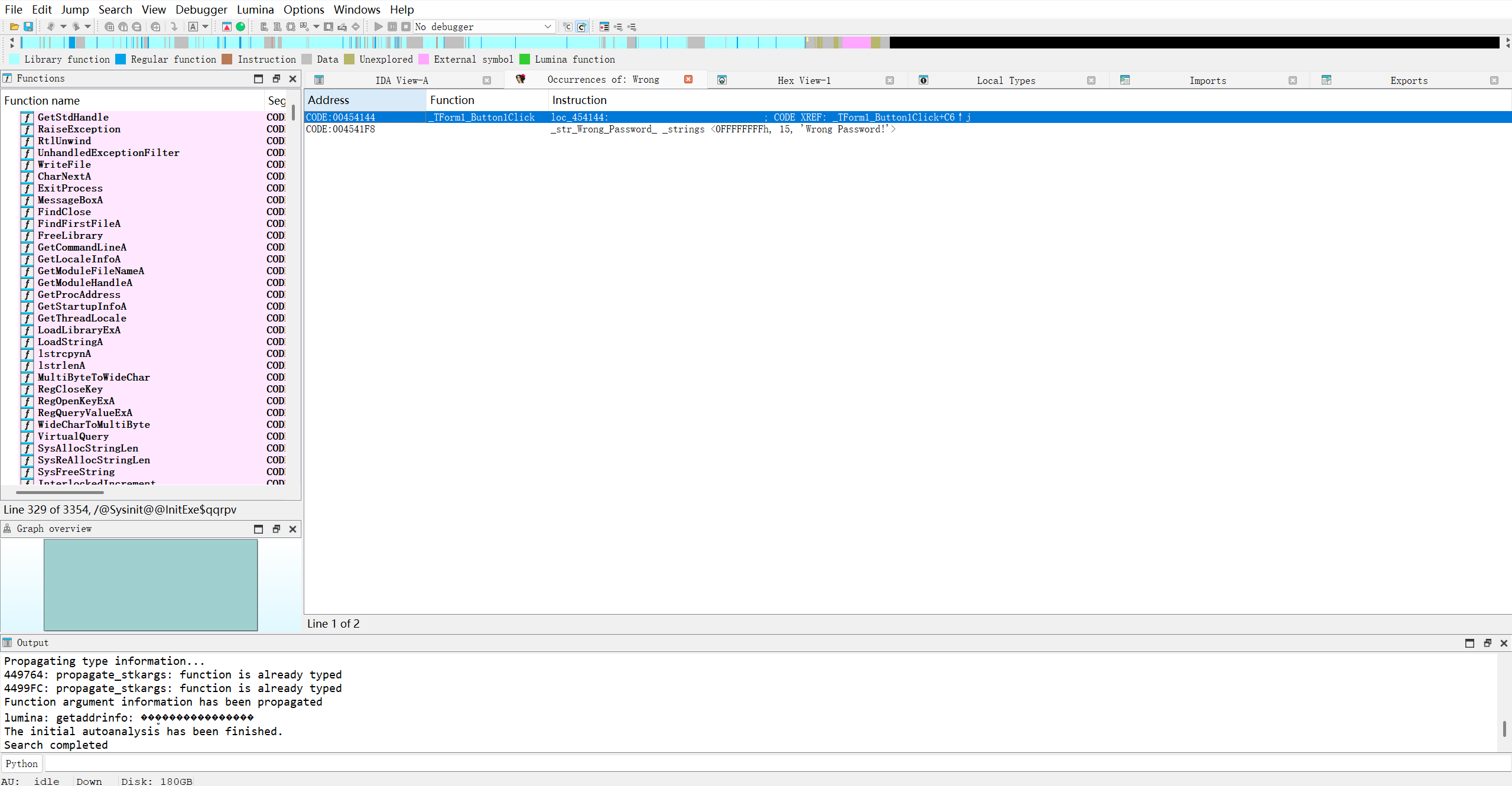
点击第二个结果会跳转到: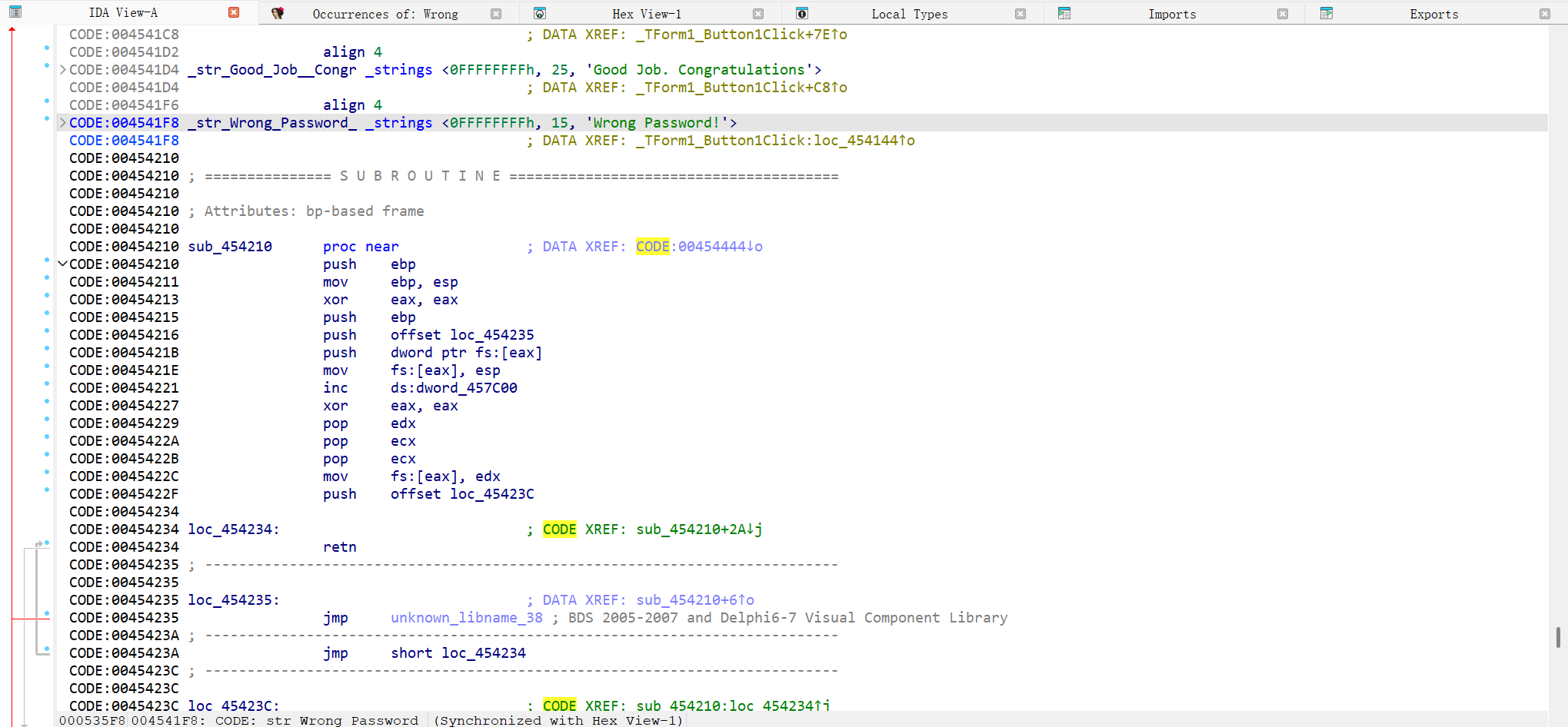
注意到它的上方有着”Goob Job. Congratulation”的字样,我们猜测这是输入成功后返回的内容,所以我们点击它下方 XREF的内容,查看这个变量在哪里被调用过,通过反汇编会得到以下内容:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43int __fastcall TForm1_Button1Click(int a1)
{
int v2; // ecx
int v3; // edx
char v4; // zf
unsigned int v6[2]; // [esp-Ch] [ebp-38h] BYREF
int *v7; // [esp-4h] [ebp-30h]
int v8; // [esp+4h] [ebp-28h] BYREF
int v9; // [esp+8h] [ebp-24h] BYREF
int v10; // [esp+Ch] [ebp-20h] BYREF
int v11; // [esp+10h] [ebp-1Ch] BYREF
int v12; // [esp+14h] [ebp-18h] BYREF
int v13; // [esp+18h] [ebp-14h] BYREF
int v14; // [esp+1Ch] [ebp-10h] BYREF
int v15; // [esp+20h] [ebp-Ch] BYREF
int v16; // [esp+24h] [ebp-8h] BYREF
int v17; // [esp+28h] [ebp-4h] BYREF
int savedregs; // [esp+2Ch] [ebp+0h] BYREF
v7 = &savedregs;
v6[1] = (unsigned int)&loc_454171;
v6[0] = (unsigned int)NtCurrentTeb()->NtTib.ExceptionList;
__writefsdword(0, (unsigned int)v6);
System::__linkproc__ LStrLAsg(&v16, &str_f[1]);
System::__linkproc__ LStrLAsg(&v15, &str_o[1]);
System::__linkproc__ LStrLAsg(&v14, &str_r[1]);
System::__linkproc__ LStrLAsg(&v13, &str_t[1]);
System::__linkproc__ LStrLAsg(&v12, &str_r[1]);
System::__linkproc__ LStrLAsg(&v11, &str_a[1]);
System::__linkproc__ LStrLAsg(&v10, &str_n[1]);
System::__linkproc__ LStrLAsg(&v9, &str___13[1]);
System::__linkproc__ LStrCatN(&v17, 8, v2, v15, v14, v13, v12, v11, v10, v9);
Controls::TControl::GetText(*(Controls::TControl **)(a1 + 760));
System::__linkproc__ LStrCmp(v8, v17);
if ( v4 )
Dialogs::ShowMessage((Dialogs *)&str_Good_Job__Congr[1], v3);
else
Dialogs::ShowMessage((Dialogs *)&str_Wrong_Password_[1], v3);
__writefsdword(0, v6[0]);
v7 = (int *)&loc_454178;
System::__linkproc__ LStrClr(&v8);
return System::__linkproc__ LStrArrayClr(&v9, 9);
}
这段代码的主要逻辑是将这些赋值变量
1 | System::__linkproc__ LStrLAsg(&v16, &str_f[1]); |
拼接成一个新的字符串 v17
1 | System::__linkproc__ LStrCatN(&v17, 8, v2, v15, v14, v13, v12, v11, v10, v9); |
然后比较输入的字符串与v17。所以我们只需要查看那些赋值字符串的具体值便可得到密码: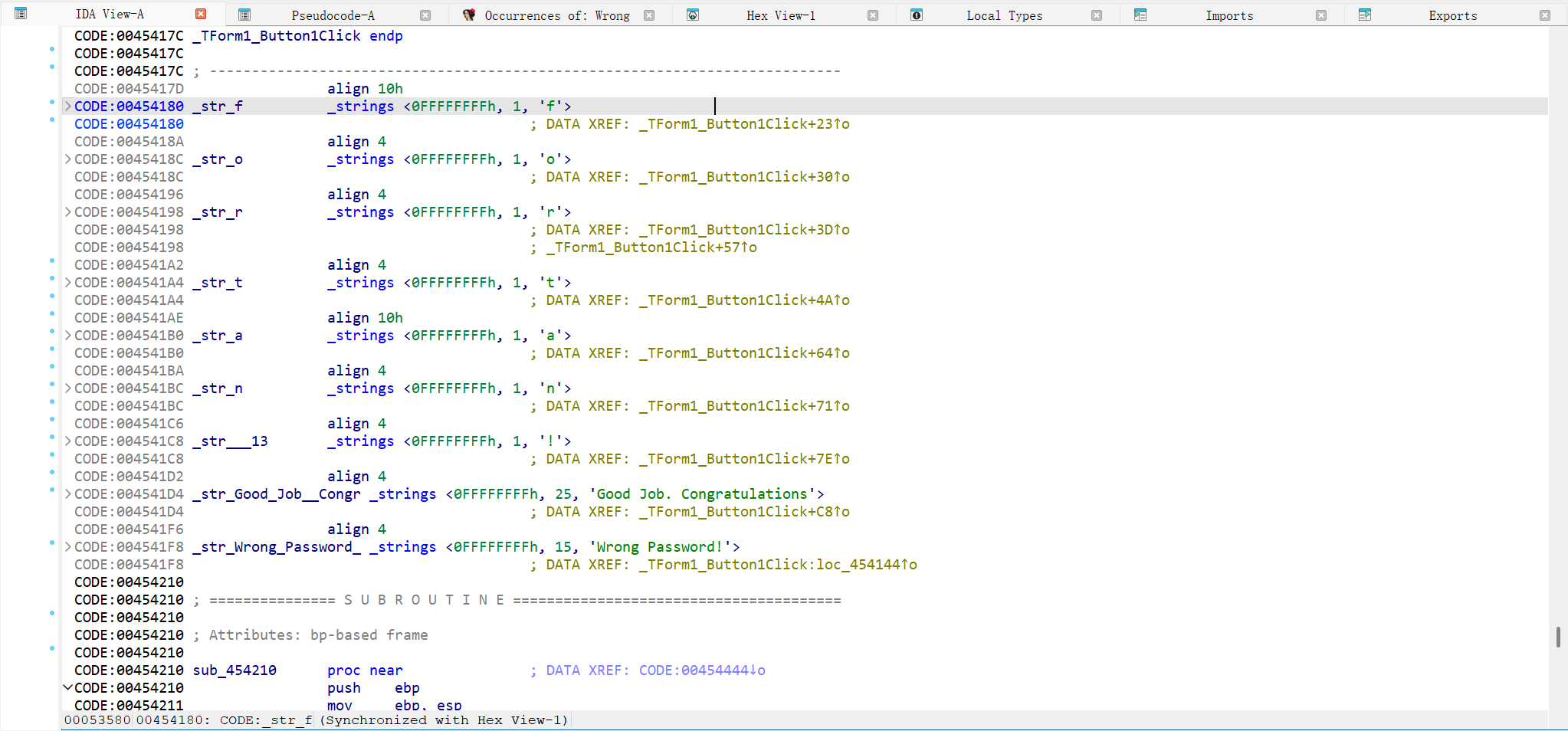
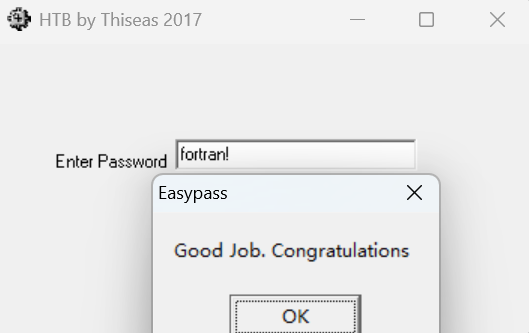
按照题目要求flag内容为:




